SECURITY
This section explains how security is managed in LSE/OS:
The Superuser Security
LSE/OS basically relies on a uid/gid based security. If uid of a task equals 0 then it is considered as the superuser task. Critical operations could only be performed by superuser tasks.
Granting ioports, Installing services for simple users
Anyway, for some user tasks that requires special access, e.g. some ioports of the system, it is possible to wrap these calls in secsrv (*) for defining a local policy.
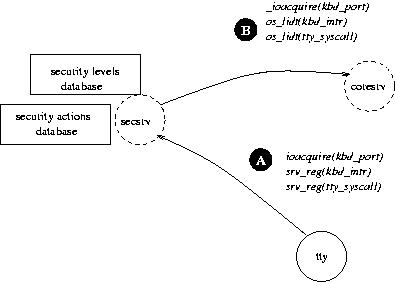
(*)Secsrv registers itself to coresrv as the Security Service (there could be only one in the system).
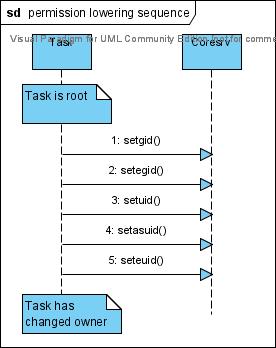
Permission Lowering
Permission lowering is quite easy but note the new syscal setasuid() that change the owner of the address space of the current task.
Permission Raising
Altough permission lowering is quite easy, permission raising is slightly more complex: TODO
Anonymity
An interesting feature of LSE/OS is to automatically clean pages with 'Z' (10101010) when they are freed. This guarantees that one task won't get information from an old task. This is also very useful for debugging.
